Interesting article about the invalidity of passwords in this day and age. Hackers are able to ascertain what our entry words/numbers are with a few simple tricks. Yet people still try to use very easy to ferret out passwords for their most valuable possession... their Identity.
Digital Domain
Goodbye, Passwords. You Arent a Good Defense.
Photo Illustration by Tony Cenicola/The New York Times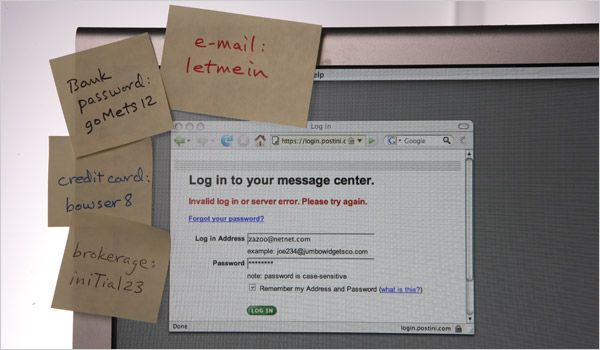
http://www.nytimes.com/2008/08/10/technology/10digi.html?ref=technology
By RANDALL STROSS
Published: August 9, 2008
THE best password is a long, nonsensical string of letters and numbers and punctuation marks, a combination never put together before. Some admirable people actually do memorize random strings of characters for their passwords and replace them with other random strings every couple of months.
Then theres the rest of us, selecting the short, the familiar and the easiest to remember. And holding onto it forever.
I once felt ashamed about failing to follow best practices for password selection but no more. Computer security experts say that choosing hard-to-guess passwords ultimately brings little security protection. Passwords wont keep us safe from identity theft, no matter how clever we are in choosing them.
That would be the case even if we had done a better job of listening to instructions. Surveys show that weve remained stubbornly fond of perennial favorites like password, 123456 and LetMeIn. The underlying problem, however, isnt their simplicity. Its the log-on procedure itself, in which we land on a Web page, which may or may not be what it says it is, and type in a string of characters to authenticate our identity (or have our password manager insert the expected string on our behalf).
This procedure which now seems perfectly natural because weve been trained to repeat it so much is a bad idea, one that no security expert whom I reached would defend.
Password-based log-ons are susceptible to being compromised in any number of ways. Consider a single threat, that posed by phishers who trick us into clicking to a site designed to mimic a legitimate one in order to harvest our log-on information. Once weve been suckered at one site and our password purloined, it can be tried at other sites.
